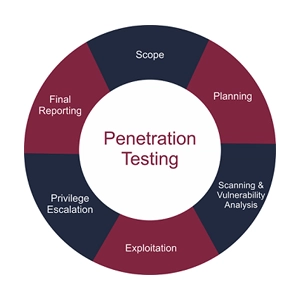
Vulnerability Management & Penetration Testing
Our Security Analysts present companies with a detailed vulnerability report and Network penetration testing enables IT departments to validate existing security controls.

Cloud Security Services
Cloud security entails securing cloud environments against unauthorized use/access, distributed denial of service (DDOS) attacks, hackers, malware, and other risks.
RBI Cyber Security Guidelines for NBFC
Application security is the process of developing, adding, and testing security features within applications to prevent security vulnerabilities against threats such as unauthorized access and modification.


Source Code Review Services
We help you assess your IT infrastructure and develop an effective plan to improve its performance.
Office 365 Security
Microsoft 365 for business plans include security capabilities, such as antiphishing, antispam, and antimalware protection.


Wireless Security
Wireless security revolves around the concept of securing the wireless network from malicious attempts and unauthorized access.
End Point Protection & Encryption Management
We help you assess your IT infrastructure and develop an effective plan to improve its performance.


